XTRF is a Polish translation management system available to install as SAAS or on your own server (both Windows and Linux). In today's article, I will keep notes on How to Setup XTRF with Apache HTTP server as a reverse proxy and SSL from Let's Encrypt
The company I'm assisting in server works has been using the XTRF translation management system since 2011 (if not earlier). A few years ago I helped to perform a major upgrade (from version 2 to version 8).
How To Install XTRF 8 on Ubuntu 18.04
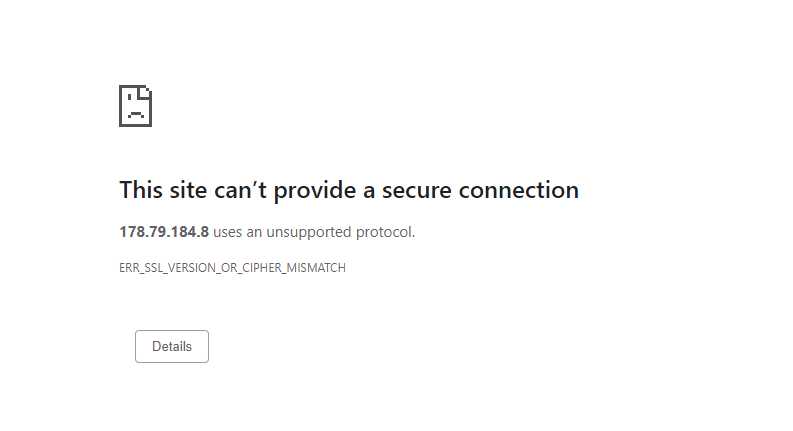
The system was launched over the internet, but recently the latest Google Chrome update stopped supporting the system saying: ERR_SSL_VERSION_OR_CIPHER_MISMATCH
XTRF runs on some Jboss server, something I'm not very well familiar with, but as a few years ago we already had a similar problem with ciphers, at the start I was looking to fix this in JBoss settings (standalone.xml)
How To Fix "Server has a weak ephemeral Dillie-Heffman public key" For Jboss Server
Though, after a few emails with the XTRF support team I got a few pointers to start with, and for my surprise, they were recommending using Apache as a reverse proxy/ here is the article from the XTRF knowledge base: SSL Certificate Installation
First things first - A record should be configured for DNS purposes, Apache with modules should be enabled, for SSL part I decided to use Let's Encrypt free SSL certificate, last but not least we should configure virtual hosts.
Let's start with Apache:
sudo nano /etc/apache2/sites-available/xtrf.conf
paste
# SSL Stapling configuration
#SSLUseStapling on SSLStaplingCache "shmcb:logs/stapling-cache(150000)"
<VirtualHost *:80>
ServerName xtrf.caucasustranslations.com
<Directory />
Options none
AllowOverride None
</Directory>
#just redirect everything to https
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
ProxyRequests Off
LogLevel notice
ServerSignature Off
ErrorLog "/var/log/apache2/error-xtrf.log"
CustomLog "/var/log/apache2/access-xtrf.eu.log" combined
RewriteCond %{SERVER_NAME} =xtrf.caucasustranslations.com
RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent]
</VirtualHost>
<VirtualHost *:443>
ServerAdmin info@caucasustranslations.com
ServerName xtrf.caucasustranslations.com
<Directory />
Options none
AllowOverride None
</Directory>
RewriteEngine On
RewriteRule ^[/]?$ /xtrf/ [R]
ProxyRequests Off
ProxyPreserveHost On
SetEnv proxy-nokeepalive 1
LogLevel notice
ServerSignature Off
# SSLEngine On
# SSLProxyEngine On
# SSLProxyVerify none
# SSLProxyCheckPeerCN off
# SSLProxyCheckPeerName off
# SSLCompression off
# SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH:ECDHE-RSA-AES128-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA128:DHE-RSA-AES128-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA128:ECDHE-RSA-AES128-SHA384:ECDHE-RSA-AES128-SHA128:ECDHE-RSA-AES128-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES128-SHA128:DHE-RSA-AES128-SHA128:DHE-RSA-AES128-SHA:DHE-RSA-AES128-SHA:AES128-GCM-SHA384:AES128-SHA128:AES128-SHA128:AES128-SHA:AES128-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4
# SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
# SSLHonorCipherOrder On
Header always set X-Frame-Options SAMEORIGIN
Header always set X-Content-Type-Options nosniff
ProxyPass /server-status !
ProxyPass / ajp://127.0.0.1:8009/
LogFormat "%h %l %u %t \"%r\" %>s %O \"%{Referer}i\" \"%{User-Agent}i\" **%T/%D** \"%{Content-Type}o\"" combined2
ErrorLog /var/log/apache2/error-xtrf_ssl.log
CustomLog /var/log/apache2/access-xtrf_ssl.log combined2
SSLCertificateFile /etc/letsencrypt/live/xtrf.caucasustranslations.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/xtrf.caucasustranslations.com/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
</VirtualHost>
now enable it
sudo a2ensite xtrf.conf
restart apache
sudo systemctl restart apache2
if there are no errors, you can proceed, if there are errors, follow the instructions on screen
Installing Certbot
How To Secure Apache with Let's Encrypt on Ubuntu 18.04
To obtain an SSL certificate with Let’s Encrypt, you need to install the Certbot software on your server. For this tutorial, we’ll use the default Ubuntu package repositories to install Certbot.
Run the following command, which will install two packages: certbot and python3-certbot-apache. The latter is a plugin that integrates Certbot with Apache, so that it’s possible to automate obtaining a certificate and configuring HTTPS within your web server with a single command:
sudo apt install certbot python3-certbot-apache
once installation is finished, enter
sudo certbot --apache
now the certbot should do the rest, and we should just answer on a few answers. If you allowed, certbot will also cofnigure virtual host and add all the nescesarry lines
Hope it helps!